Follow the steps below to complete device enrollment when demonstrating personal devices in the Cisco ISE demonstrations.
Joining nodes to a Cisco ISE deployment requires the admin nodes to trust the SSL certificate on the new node. The SSL certificate that must be trusted is the one used for the Admin portal. Self-signed or private certificates (e.g. Local enterprise CA) are desired for the Admin portal because of the way BYOD works when using the ISE server as a CA. Cisco ISE presents the Portal certificate on TCP port 8443 (or the port that you have configured for portal use). Note Step 1 Create a Certificate Signing Request and Submit the CSR to a Certificate Authority, on page 20. You must choose a Certificate Group Tag that you have already defined or create a new one for the portal. For example, mydevicesportal.
Depending on the software version of your device, the steps below may vary.
- Installing an enterprise PKI certificate for use in cisco ISE. Check out the blog!
- Symptom: Unable to delete certificate with Default Portal Certificate group tag. Error: Portal certificate that is currently in use cannot be deleted. Change the portal configuration and try again. Conditions: All portals seen from GUI mapped to different group tag. One of the previous portals on ISE 1.3 deleted from GUI.
Scenario Credentials
The table below contains the scenario credentials that will be needed to complete device enrollment.
Table 1. Scenario Credentials
| Scenario / Vertical | Username | Password | Access Level | Connections Center Webpage |
| Healthcare | doctor | C1sco12345 | Tier 1 – Full | http://health.dcloud.cisco.com |
| Healthcare | nurse | C1sco12345 | Tier 2 – Limited Access | http://health.dcloud.cisco.com |
| Education | dean | C1sco12345 | Tier 1 – Full Access | http://edu.dcloud.cisco.com |
| Education | professor | C1sco12345 | Tier 2 – Limited Access | http://edu.dcloud.cisco.com |
| Federal | captain | C1sco12345 | Tier 1 – Full Access | http://federal.dcloud.cisco.com |
| Federal | officer | C1sco12345 | Tier 2 – Limited Access | http://federal.dcloud.cisco.com |
| Corporate | manager | C1sco12345 | Tier 1 – Full Access | http:/corp.dcloud.cisco.com |
| Corporate | employee | C1sco12345 | Tier 2 – Limited Access | http:/corp.dcloud.cisco.com |
| N/A | itadmin | C1sco12345 | Full Demo Access |
Apple iOS Devices

If prompted while going through BYOD for a PIN or password, enter your device specific pin/password.
Follow the steps below to enroll Apple iOS devices.
- Connect to the wireless network.
- Go to Settings > Wi-Fi and connect to the network dCloud-Guest.
- Open a website to be redirected to the Guest Portal to perform onboarding.
- Open your built-in browser (Apple Devices: Safari)
- Attempt to connect to your Demo Scenario page (ex: corp.dcloud.cisco.com) and you will be redirected to the Guest portal.
If this doesn’t work try another http site, for example http://cnn.com
Be sure that the website you attempt to open uses HTTP, as HTTPS redirection is not supported in this demo.
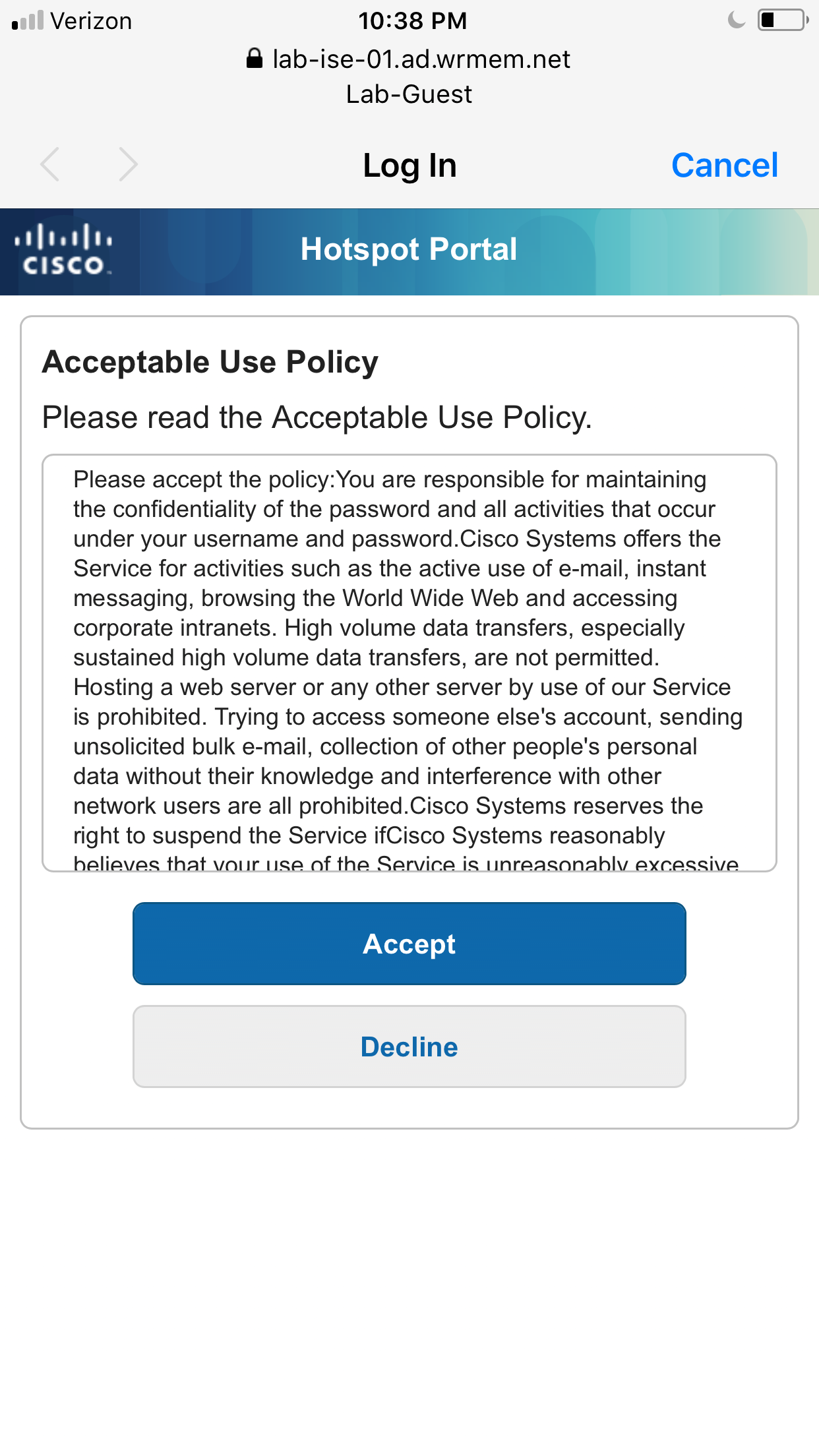
- On the guest portal, login with the user credentials for your selected scenario, as shown in Table 1.
- Click Accept to accept the Acceptable Use Policy.
- Click Start on the BYOD welcome page.
- Fill out the device information and click continue.
- Click Launch Apple Profile and Certificate Installers Now
- On the Install Profile screen click Install to install the digital certificate for User Trust RSA Certification Authority.
- Click Install on the Warning message that pops up.
- Click Done on the profile installed screen.

- Click Install once again on the Install Profile screen to install the profile service, then click Install Now to verify
The first profile installation installs the CA root certificate, while the second profile installation installs the individual device certificate and the wireless settings needed to connect to the secure network.
- Click Done on the profiled installed screen.
- You are redirected to the Success page. Go to Settings > Wi-Fi forget the dCloud-Guest network and you should automatically connect to network dCloud-Registered.
Please see the following link with known issues with different clients connecting to the ISE demos – https://communities.cisco.com/docs/DOC-75784
Android Devices
If prompted while going through BYOD for a PIN or password, enter C1sco12345.
Some Android devices require an SD card to store security certificates. Please be aware that some Android devices might not work with this demonstration. Android is open source across cellular carriers and device vendors. Some vendors update their code more frequently than others. Compatibility with all devices cannot be guaranteed.
Follow the steps below to enroll Android devices.
- Go to Settings > Wi-Fi and connect to the network dCloud-Guest.
- Launch the default Android web browser and access the Connections Center Webpage for your selected scenario as shown in Table 1. Accept any HTTPS warnings if necessary.
- Login with the username and password for your selected scenario. You are redirected to the self-provisioning page.
- Click Accept to accept the AUP.
- Fill out the device information and click Continue.
- Close you web browser and use the Google Play Store application on your device to download the Cisco Network Setup Assistant. If prompted for a Pin, enterC1sco12345.
Because Android is an open platform, we cannot account for all variations of the product.
Open Network Setup Assistant and click Start. Wait for your Android to be provisioned and joined to the correct network.
- On your device, in WiFi Settings, select the dCloud-Guest SSID and forget the SSID.
- Connect to the dCloud-Registered SSID.
You cannot use a randomized MAC address (Android default) when logging in because this causes a different MAC to be used for different SSIDs login and results in failure to authenticate to networks. You must use the actual MAC address of the device.
Mac OSX Workstations
- Connect to the wireless network.
- Click the wireless icon at the top of the desktop and connect to the network dCloud-Guest.
- Open a website to be redirected to the Guest Portal to perform onboarding.
- Open your built-in browser (Apple Devices: Safari).
- Attempt to connect to your Demo Scenario page (ex: corp.dcloud.cisco.com) and you will be redirected to the Guest portal.
- If you are prompted with a certificate warning, click continue.
Be sure that the website you attempt to open uses HTTP, as HTTPS redirection is not supported in this demo.
- On the guest portal, login with the user credentials for your selected scenario, as shown in Table 1.
- Click Accept to accept the AUP.
- Click Start on the BYOD welcome page.
- Fill out the device information and click continue.
- You are brought to the install page. The Cisco Network Setup Assistant will automatically begin downloading in the background. When it is done, open your downloads folder in finder and launch the SPW.tar.gz which extracts into cisco_network_setup_assistant.dmg.
- Double click the Cisco Network Setup Assistant icon. You may be prompted with a warning that “Cisco Network Setup Assistant” is an application downloaded from the internet. Click Open on this warning to launch the application.
You may need to change security settings in OSX in order to run the Cisco Network Setup Assistant application. By default, OSX will only allow you to install applications from Apple. If you get an error that the Cisco Network Setup Assistant cannot be run, you likely need to change security settings. To do this go to System Preferences then Security & Privacy. At the bottom, in the section labeled Allow apps downloaded from: select the Anywhere radio button
- Click Start in the Network Setup Assistant. Click Continue on the verify certificate popup if necessary.
- Enter your local computer credentials and click OK. These are the same credentials you use to login to your Mac. You may need to enter your credentials twice during this process, depending on your version of OSX due to security changes in OSX.
- Click Exit on the network setup assistant after it successfully completes
- OSX should automatically switch you to the dCloud-Registered network. Verify you are now connected to the dCloud-Registered network
- Open Safari and enter the Connections Center Webpage that corresponds to your selected scenario (Table 1).
Windows Workstations
You must use the default Windows wireless client for this demo.
- Connect to the wireless network.
- Click the wireless icon and connect to the network dCloud-Guest.
- Open a website to be redirected to the Guest Portal to perform onboarding.
- Open your built-in browser (Windows: IE/EDGE).
- Attempt to connect to your Demo Scenario page (ex: corp.dcloud.cisco.com) and you will be redirected to the Guest portal.
- If you are prompted with a certificate warning, click continue.
Be sure that the website you attempt to open uses HTTP, as HTTPS redirection is not supported in this demo.
- On the guest portal, login with the user credentials for your selected scenario, as shown in Table 1.
Ise Guest Portal Certificate
- Click Accept to accept the AUP.

- Click Start on the BYOD welcome page.
- Fill out the device information and click continue.
- The Cisco Network Setup Assistant will be downloaded. If you are prompted, save the file NetworkSetupAssistant.exe to your Downloads folder.
- Launch the NetworkSetupAssistant.exe installer that was downloaded. Click Run on any security warnings.
- Click Start. Proceed through any certificate warning messages, if necessary.
- Click Exit on the network setup assistant after it successfully completes.
- Windows should automatically switch you to the dCloud-Registered network. Verify you are now connected to the dCloud-Registered network
- Open IE or Firefox and enter the Connections Center Webpage that corresponds to your selected scenario (Table 1).
I’ve noticed an odd error where my public certificate had incomplete certificate chain. This may cause issues with PxGRID integration and BYOD provisioning.
Both Intermediate and root certificates were present in the trusted certificate store however there appeared to be 2 primary roots
and one of them obviously is incorrect braking the chain. So the easy way to find out which one is bad is to export your identity certificate and view chain on your computer.
Once exported, rename the file from PEM to CER extension and open it. Go to Certification Path to view complete chain. We see certificate and chain checked out ok.
Select Root certificate and record either Serial Number or Expiration date. Here we can see that correct root should have 7/16/2036 Expiration Date.
Checking back on ISE select root certificate and we see a different expiration date meaning root certificate is incorrect causing chain to be incomplete.
To fix it remove incorrect root certificate. Select it and delete under ISE Trusted Certificates page. Of course changes should be done in the Maintenance Window.
My Guest Portal
Once removed, the chain will appear as intact right away but it is strongly recommended to restart all ISE nodes anyway to rebuild it properly.
